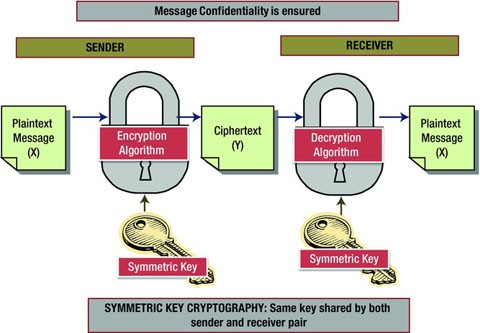
Keys Algorithm Among Us, Https Eprint Iacr Org 2005 018 Pdf
Keys algorithm among us. Among Us lately becomes an very by popular games, maybe it is because its very addictive game to play. Become an impostor is the dream by every player in Keys algorithm among us game. Because you can toy another crewmate and It is fun to see friends fighting among others to vote for the impostor, and sometimes they start of to argue which player Is the true Impostor Keys Algorithm Among Us.
More From Keys Algorithm Among Us
- Orange Was Ejected Among Us
- How To Get Knife Hat In Among Us
- How To Update Among Us On Android
- Play Among Us On Pc Online
- Imposter Among Us Adalah
If you re searching for download Imposter Among Us Adalah you've arrived at the perfect place. We have 104 download source about imposter among us adalah adding apk, cheat, cheat apk, wallpapers, and more. In such page, we additionally have number of mp3 available. Such as png, jpg, animated gifs, pic art, symbol, blackandwhite, translucent, etc.
Incoming Search Terms:
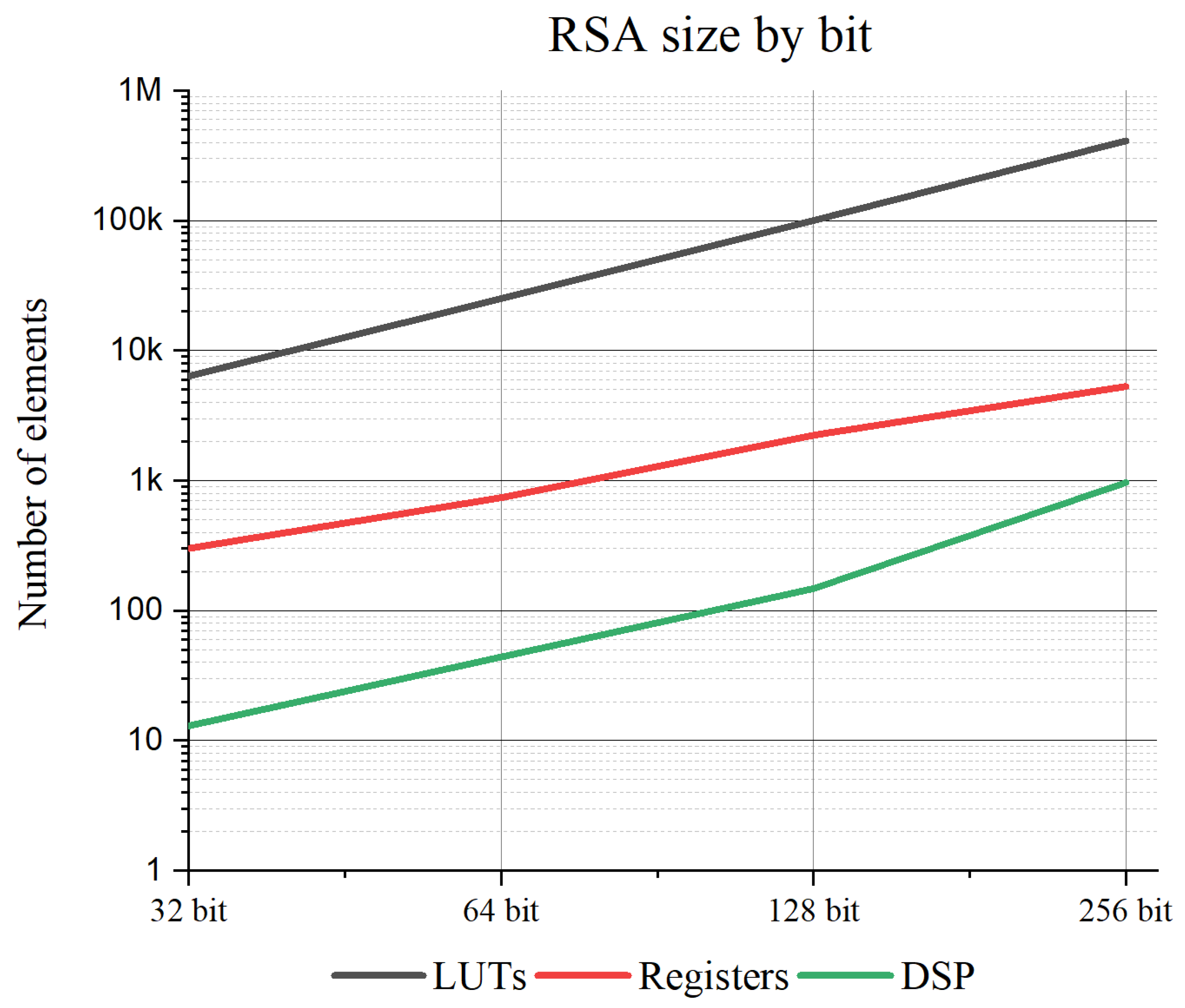
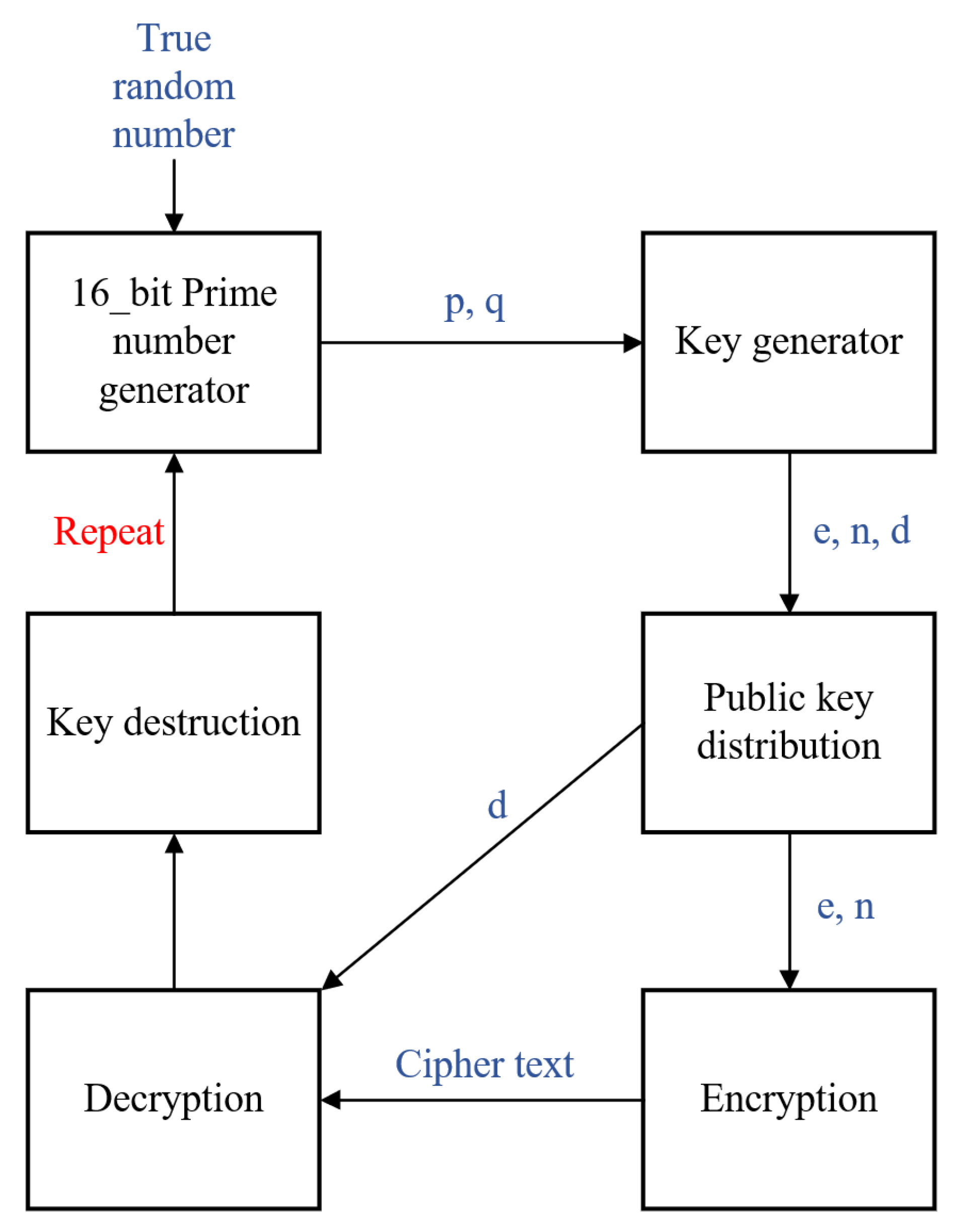
- Pdf High Speed Implementation Of Rsa Algorithm With Modified Keys Exchange Imposter Among Us Adalah,
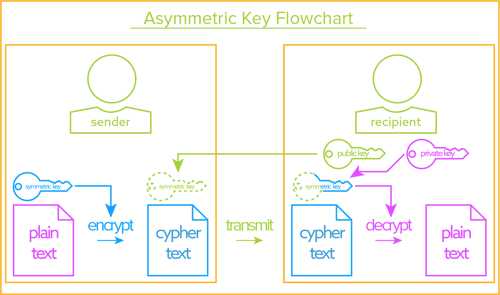
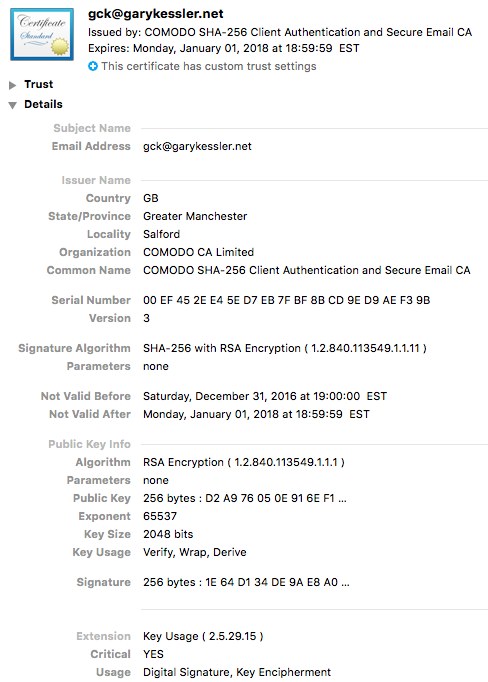
- The Definitive Guide To Encryption Key Management Fundamentals Imposter Among Us Adalah,
- Among Us Tips To Win As Imposter And Get Away With Murder Gamespot Imposter Among Us Adalah,
- Quantum Computing And The End Of Encryption Hackaday Imposter Among Us Adalah,
- Https Eprint Iacr Org 2005 018 Pdf Imposter Among Us Adalah,
- Guess Why We Re Moving To 256 Bit Aes Keys 1password Imposter Among Us Adalah,